Symbol: Erik Mclean
Researchers at web page safety company Sucuri have come upon a brand new WordPress malware utilized by danger actors to scan for and establish WooCommerce on-line stores with numerous consumers to be centered in the long term Magecart assaults.
WooCommerce is an open-source WordPress plugin with over five million lively installs and designed to make it simple to run e-commerce websites that can be utilized to “promote anything else, anyplace.”
Attacking WooCommerce on-line shops isn’t one thing new as proven via earlier assaults that have been making an attempt to hack into on-line shops via brute-forcing admin passwords with the tip purpose of harvesting bank cards (additionally identified as Magecart assaults), as detailed via Sanguine Safety’s Willem de Groot two years in the past.
Buggy plugins used to hack e-shops
To hack into WooCommerce-based webshops and drop this new malware, the hackers are profiting from safety vulnerabilities present in different WordPress plugins.
Via exploiting those flaws, they’ll be capable to get entry to the e-store’s inside construction, uncover if the web site is the usage of the WooCommerce platform, and therefore accumulate and exfiltrate data in regards to the WooCommerce set up to attacker-controlled servers.
“It’s vital to notice that via default, the WooCommerce plugin does now not shop cost card knowledge — attackers can’t merely thieve delicate cost main points from the WordPress database,” Sucuri malware researcher Luke Leal explains.
The malware is put in within the type of a malicious PHP script as a part of the post-exploit level that follows the hit compromise of an inclined WordPress web site.
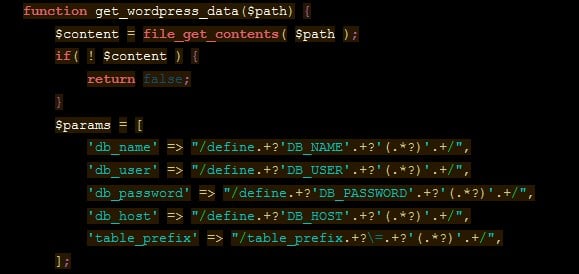
This script is used for scanning for different WordPress objectives, to hook up with their databases, and to question them for WooCommerce knowledge.
It additionally extracts MySQL database credentials that may permit it to get entry to the compromised shop’s WordPress database and run SQL queries designed to assemble WooCommerce-specific knowledge together with the shop’s overall selection of orders and bills.
Magecart reconnaissance
Whilst Sucuri didn’t element what this knowledge can be utilized for, the malware operators can use the stolen order and cost knowledge to come to a decision if it is price deploying skimmers in particular designed to focus on WooCommerce e-shops.
This may let them focal point their ‘efforts’ on on-line shops that obtain numerous site visitors and orders and keep away from losing their time on e-commerce shops which can be both inactive or should not have numerous consumers.
One such Magecart marketing campaign focused on the simplest WooCommerce shops used to be noticed via Sucuri one month in the past, with the bank card thieves being noticed whilst injecting a devoted JavaScript-based card-skimmer that harvested bank card numbers and card safety codes (CVVs).
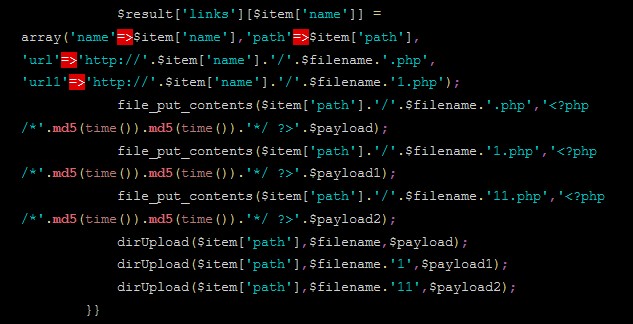
The WordPress malware may also deploy 3 backdoors on inflamed web pages, one thing that may be very helpful if the attackers ever come to a decision to come back again a deploy an internet skimmer.
“This malware is a brilliant instance of attackers leveraging unauthorized get entry to resolve new, doable objectives inside of compromised web hosting environments,” Leal concluded.
“It additionally demonstrates how cross-site contamination can happen growing more than one backdoors in directories out of doors of the present inflamed web page listing.”