The hacking workforce builds new Ketrum malware from recycled backdoors
The hacking team builds new Ketrum malware historically believed to be operating out of China has advanced new malware dubbed Ketrum by the use of merging choices and provide code from their older Ketrican and Okrum backdoors.
The cyber-espionage movements of the Ke3chang complicated chronic threat (APT) workforce (moreover tracked as APT15, Vixen Panda, Playful Dragon, and Royal APT) transfer as far as 2010 consistent with FireEye researchers.
Ke3chang’s operations objective relatively a large number of military and oil business entities, along with government contractors and Eu diplomatic missions and organizations.
New malware with old-fashioned choices
A brand spanking new document from Intezer researchers shows how they discovered three Ketrum backdoor samples this month on the VirusTotal platform and compare them with the Chinese language cyberspies after noticing that it reused each and every code and features from Ke3chang’s Ketrican and Okrum backdoors.
The Ketchum samples they analyzed showed that the hacking workforce hasn’t deviated from their previous documented Ways, Techniques, and Procedures (TTP).
The new backdoor, however, follows the equivalent principle of providing a fundamental backdoor that can be used by the use of Ke3chang operators to take keep an eye on of a targeted device, connect with it from a remote server, and manually transfer all the way through the other steps of the operation.
As they further found out, the malware hooked as much as a Chinese language language-based command and keep an eye on (C2) server that ceased operating during mid-May after the Ketrum samples had been spotted.
Feature comparison between the older Ketrican and Okrum backdoors and the new Ketrum backdoor samples is embedded beneath.
| Backdoor options | Ketrican | Okrum | Ketrum1 | Ketrum2 |
| Identify installed proxy servers and use them for HTTP requests | ❌ | ✅ | ✅ | ✅ |
| Specific folder retrieval the use of the registry key [HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerShell Folders] |
✅ | ❌ | ✅ | ✅ |
| The response from the server is an HTTP internet web page with backdoor directions and arguments built-in throughout the HTML fields | ✅ | ❌ | ❌ | ✅ |
| Backdoor directions are decided by the use of a hashing price won from C2 | ❌ | ✅ | ❌ | ❌ |
| Verbal exchange with the C&C server is hidden throughout the Cookie and Set-Cookie headers of HTTP requests | ❌ | ✅ | ✅ | ❌ |
| Impersonate a logged-in shopper’s protection context | ❌ | ✅ | ✅ | ❌ |
| Create a duplicate of cmd.exe in their running checklist and use it to interpret backdoor directions | ✅ | ❌ | ✅ | ❌ |
| Standard Ke3chang backdoor functionalities – download, upload, execute knowledge/shell directions and configure sleep time | ✅ | ✅ | ✅ | ✅ |
| Screenshot-grabbing capacity | ❌ | ❌ | ✅ | ❌ |
Malware minimalism
“Every Ketrum samples resemble a an equivalent construction to previous Ke3chang tools, except for low-level implementation and use of instrument APIs,” Intezer outlined. “Even throughout the two Ketrum samples, there are diversifications between the low-level APIs used to succeed in the equivalent capacity.”
While the Ketrum 1 development that were given right here with a faked January 7, 2010, timestamp shows that the hacking workforce implemented a variety of the choices available throughout the two older backdoors, the newer Ketrum 2 variant drops a variety of the fluff and saved the most common Ke3chang backdoor functionalities.
When the use of the minimalist Ketrum 2 backdoor during no doubt one among their attacks, the operators can download, upload, and execute knowledge/shell directions, as well as, to configure sleep time for compromised units, alternatively, they not can take show snapshots.
“The gang continues to morph its code and switch fundamental functionalities in their relatively a large number of backdoors,” Intezer concludes. “This method has been running for the group for years and there’s no indication however that it’s going to deviate from this modus operandi.”
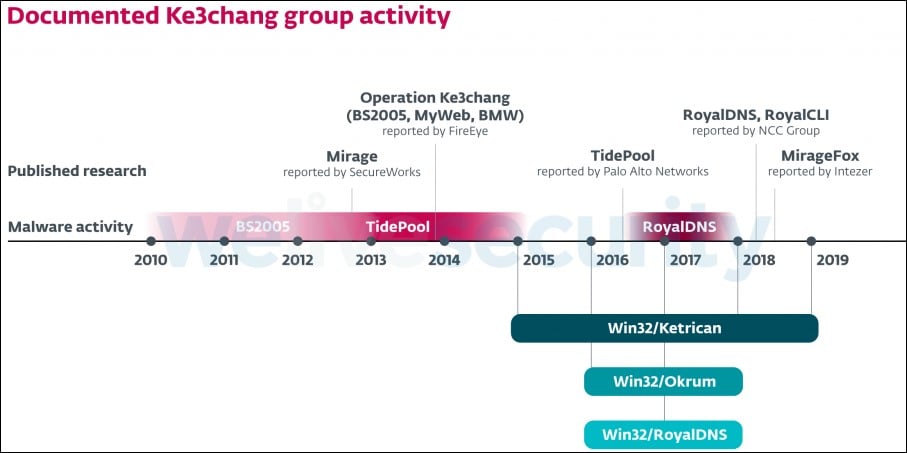
ESET researchers had been those that spotted the group’s Ketrican and Okrum backdoors in 2015 and 2016, respectively, while investigating attacks towards various diplomatic missions international.
Between 2012 and 2015 Ke3chang used the TidePool RAT-like malware to assemble knowledge after exploiting the CVE-2015-2545 Microsoft Place of work protection flaw, while from 2016 to 2017 the group deployed the RoyalCLI and RoyalDNS backdoors in attacks targeting the UK government, attempting to steal military tech and governmental knowledge.
In 2018, Ke3chang started the use of every other implant, a variant of the Mirage A ways-flung Get right to use Trojan (RAT) dubbed MirageFox.
Indicators of compromised (IOCs) and extra details regarding the new Ketrum umbrella of malware will also be found out inside Intezer’s document.





