Microsoft has issued a security advisory to mitigate the NXNSAttack vulnerability in DNS servers that can be used to escalate a single DNS request in a DDoS attack against authoritative DNS servers.
In a new paper, researchers from Tel Aviv University and The Interdisciplinary Center have uncovered a new vulnerability called NXNSAttack that “could be used to mount a destructive attack against both recursive resolvers and authoritative servers.” ”
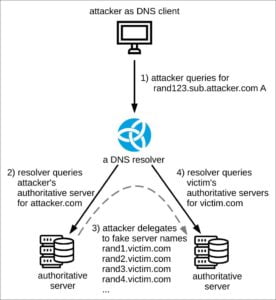
In a nutshell, NXNSAttack works by an attacker sending a DNS request to a recursive server for a domain under the attacker’s control. Since this recursive server does not have authority to resolve the request, it sends a query to the authoritative DNS server for the attacker’s domain.
The authoritative server is also under the attacker’s control and will respond with a list of servers that the original resolver should query. However, this list of servers will be the target of a DNS DDoS attack, which will now be queried.
If multiple requests are made in this way, it could allow an attacker to DDoS attack an authoritative DNS server and render it unresponsive.
The attack is illustrated by the image below created by Nic.cz in its blog post regarding the NXNSAttack attack.
According to the researchers, this attack has “an amplification factor of more than 1620x the number of packets changed by the recursive resolver,” which could be disastrous for their targets.
To address this vulnerability, DNS server developers have started issuing advisories and patches for their software. Below is a list of currently known advices.
- DNS Server Published Advisory Advisory
- ISC BIND Security Advisor CVE-2020-8616
- NLnet Labs Unbound CVE-2020-12662
- NIC.CZ Not Resolver Blog Post CVE-2020-12667
- PowerDNS Security Advice
- Microsoft ADV200009 | Windows DNS Server Denial of Service Vulnerability
More information about NXNSAttack can be found at the NXNSAttack.com site created by the researchers, and Nic.cz’s blog post is a recommended read.
Mitigating the NXNSAttack Attack on Windows DNS Servers
Microsoft’ ADV200009 | . NXNSAttack released the Windows DNS Server Denial of Service vulnerability yesterday with ‘DNS Attack Mitigation’ security advisory.
“An attacker who successfully exploited this vulnerability could cause the DNS Server service to become unresponsive.”
“To exploit this vulnerability an attacker would need to have access to at least one client and a domain that responds with a large amount of referral records without glue records pointing to the external victim subdomain. When resolving the name, for each referral record found, the resolver contacts the victim domain. This action can generate a large number of communications between the recursive resolver and the victim’s authoritative DNS server, leading to a distributed denial of service. (DDoS) attack,” explains Microsoft’s ADV200009 Security Advisor.
To mitigate this attack, Microsoft recommends that administrators use the Set-DnsServerResponseRateLimiting PowerShell cmdlet to enable response rate limiting.
Response rate limiting is a configuration option used by DNS servers to prevent them from being used in DDoS attacks using DNS amplification.
When enabled, this setting will limit the number of responses or errors that a DNS server can send to a DNS client in one second.
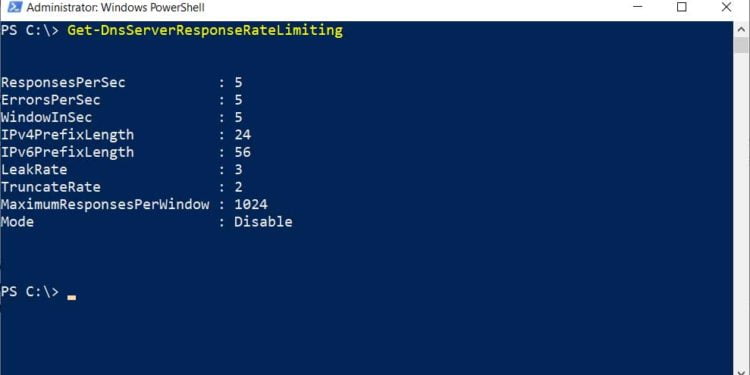
To check your current response rate limiting setting, you can run the Get-DnsServerResponseRateLimiting PowerShell command.
As you can see from the above default settings, the Windows DNS server will only respond to a client five times within one second.
If you want to increase or decrease this amount, you can do so with the Set-DnsServerResponseRateLimiting PowerShell command.
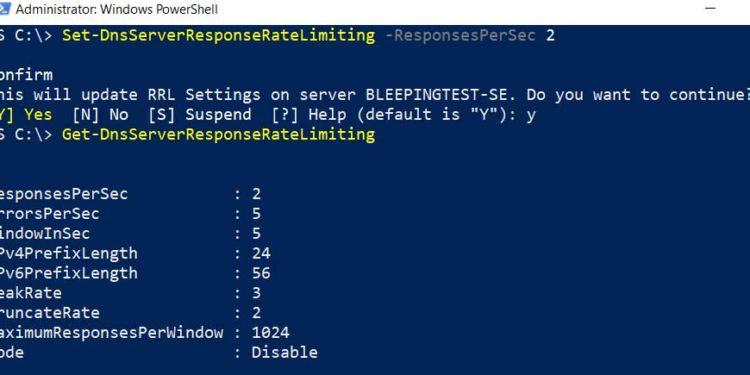
For example, to reduce the number of responses to two per second, you would issue the following command:
Set-DnsServerResponseRateLimiting -ResponsesPerSec 2
A similar command can be used to reduce the number of errors to two per second:
Set-DnsServerResponseRateLimiting -ErrorsPerSec 2It should be noted that utilizing the Response Rate Limiting feature will prevent a Windows DNS server from being used in a DNS amplification attack against another client. It will not, though, protect the server itself from being impacted.
Unfortunately, Microsoft has not specified what the recommended values are to mitigate this attack.